Threat & Vulnerability Management
for Small Businesses
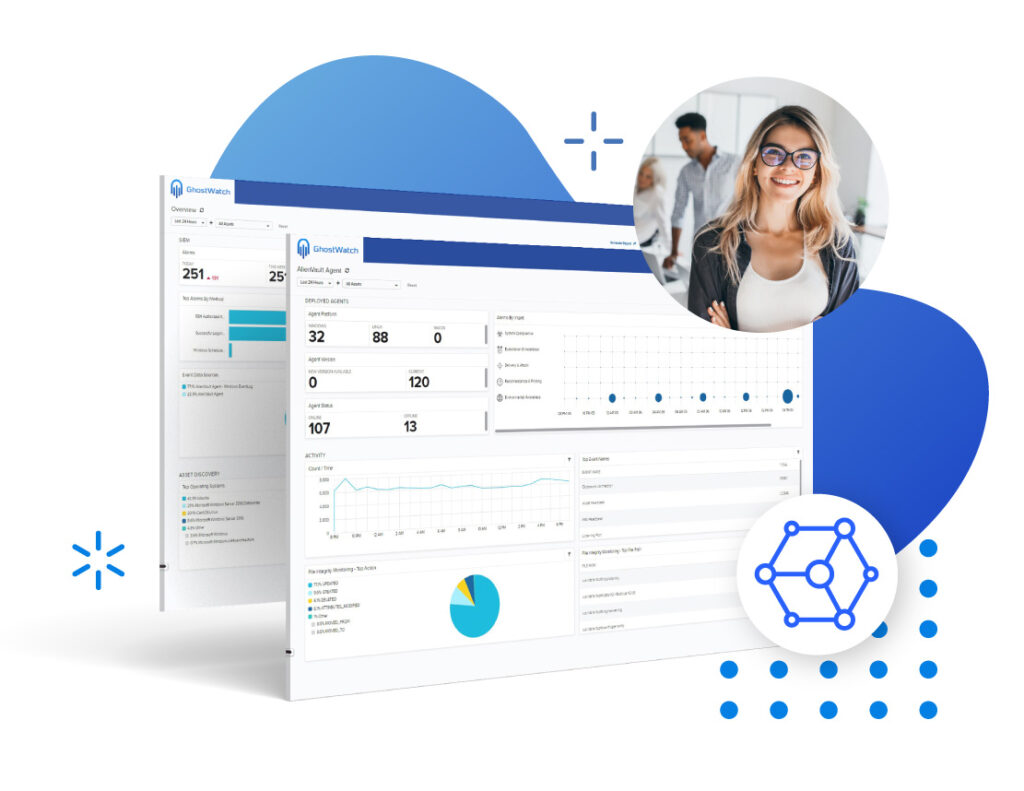
GhostWatch consolidates threat detection capabilities like network IDS and host IDS with granular asset information, continuous vulnerability assessment, and behavioral monitoring.
Trusted by Leading Brands



Threat Management
Consolidating threat detection capabilities like network IDS and host IDS with granular asset information, continuous vulnerability assessment, and behavioral monitoring provides a comprehensive view for timely and effective response.
Advanced Endpoint Detection

Intrusion
Detection
Threat
Analysis
Ransomware
Detection
Advanced Endpoint Threat Prevention

Advanced Remediation Management
See how we detect and investigate intrusions, identify and prioritize vulnerabilities, and monitor cloud and on-premise environments.
Vulnerability Management
GhostWatch detects vulnerabilities in critical assets and assigns a risk factor to each vulnerability corresponding with the Common Vulnerability Scoring System.
Vulnerability Assessment and Remediation
Continuously identify insecure configurations, unpatched, and unsupported software.
- On-demand and scheduled scanning and reporting
- Vulnerability scanning with actionable information
- Context for security incident response
Vulnerability Scanning
A simplified and more manageable network vulnerability scanner. GhostWatch stays ahead of attackers with advanced features.
- Simple configuration and scheduling
- Intuitive dashboard and reporting
- Regular updates
Threat Intelligence
GhostWatch detects the latest global threats
and prioritizes responses
Data Exfiltration Detection
Prevents leakage of sensitive and proprietary data
Real-Time Botnet Detection
Identify infection, compromise, and misuse of assets
Command-and-Control Traffic Identification
Identify compromised systems communicating with malicious hackers
IP, URL, and Domain Reputation Data
Prioritize response efforts by identifying known bad actors and infected sites
APT (Advanced Persistent Threat) Detection
Detect targeted attacks often missed by other defenses
Dynamic Incident Response and Investigation
Specific directives to respond to each alert